안녕하세요 늑대양 입니다

매주 일요일 오전 10시 온오프라인 믹스 방식으로 테라폼 자격증 스터디를 진행하고 있습니다.
관련된 내용은 아래의 유튜브 채널 라이브 스트림 탭에서 확인하실 수 있습니다.
https://www.youtube.com/@TV-eu5yk/streams
늑대양TV
www.youtube.com
구독 과 좋아요~🙂

전일(20240505) 진행된 HashiCorp Terraform Associate(HCTAO-003) 스터디 2주차 내용을 전달드리도록 하겠습니다.
해당 주차에 진행된 학습 목표는 아래와 같습니다
학습 목표:
- Understand Infrastructure as Code (IaC) concepts
- Explain what IaC is
- Describe advantages of IaC patterns
- Understand the purpose of Terraform (vs other IaC)
- Explain multi-cloud and provider-agnositc benefits
- Explain the benefits of state
- Understand Terraform basics
- Install and version Terraform providers
- Describe plugin-based architecture
- Write Terraform configuration using multiple providers
- Describe how Terraform finds and fetches providers
아래는 스터디에 사용한 노션을 편집한 내용입니다.
테라폼 자격증을 공부하시는 분들에게 도움이 되었으면 좋을 것 같습니다 🤗
Understand Infrastructure as Code (IaC) concepts
Explain what IaC is:
https://developer.hashicorp.com/terraform/intro
What is Terraform | Terraform | HashiCorp Developer
Terraform is an infrastructure as code tool that lets you build, change, and version cloud and on-prem resources safely and efficiently.
developer.hashicorp.com
What is Terraform?:
- HashiCorp Terraform is an infrastructure as code tool that lets you define both cloud and on-prem resources in human-readable configuration files that you can version, reuse, and share.
- Terraform can manage low-level components like compute, storage, and networking resources, as well as high-level components like DNS entries and SaaS features.
How does Terraform work?
- Terraform creates and manages resources on cloud platforms and other services through their application programming interfaces (APIs).
- Providers enable Terraform to work with virtually any platform or service with an accessible API.

- HashiCorp and the Terraform community have already written thousands of providers to manage many different types of resources and services.
Terraform Registry
registry.terraform.io
- Core Terraform workflow (3 stages)
- Write
- Plan
- Apply
Why Terraform?
- Manage any infrastructure
- Track your infrastructure
- Automate changes
- Standardize configurations
- Collaborate
Infrastructure as Code in a Private or Public Cloud
Infrastructure as Code in a Private or Public Cloud
Successfully managing the lifecycle of infrastructure is hard, and the impact of poor management decisions can be significant, ranging from financial and reputational losses to even loss of life when considering government and military dependencies on infr
www.hashicorp.com
- 2020.01.23 작성된 내용
- For example, as companies move their operations to the cloud they tend to manage their cloud infrastructure the same way they managed their on-premise physical hardware, by logging into their virtual infrastructure’s web interface, or directly onto a system and applying changes via GUI or CLI.
- What is IaC? It is infrastructure (CPUs, memory, disk, firewalls, etc.) defined as code within definition files. But why change how we define and build infrastructure?
- More modern tools accepted code that was both human and machine readable, and provided additional benefits.
- They simplified code testing, could apply and track the changes between iterations, and most importantly they enabled teams to reuse components (e.g. modules) of code across different projects.
- It’s no wonder that IaC has developed such a significant following and adoption.
IaC and the Infrastructure Lifecycle
- So how does IaC fit into the infrastructure lifecycle?
- IaC can be applied throughout the lifecycle, both on the initial build, as well as throughout the life of the infrastructure.
- Commonly, these are referred to as Day 0 and Day 1 activities.
- “Day 0” code provisions and configures your initial infrastructure.
- If your infrastructure never changes after the initial build (no OS updates, no patches, no app configurations, etc.) then you may not need tools that support subsequent updates, changes, and expansions.
- “Day 1” refers to OS and application configurations you apply after you’ve initially built your infrastructure.
- IaC makes it easy to provision and apply infrastructure configurations, saving time.
- It standardizes workflows across different infrastructure providers (e.g., VMware, AWS, Azure, GCP, etc.) by using a common syntax across all of them.
- IaC makes it easy to understand the intent of infrastructure changes, because it can span multiple files, allowing human operators to organize the code based on the intent.
# 코드 예시
# Provision an Amazon VPC
resource "aws_vpc" "default" {
cidr_block = "10.0.0.0/16"
}
# To apply initial configurations - start a web server
provisioner "remote-exec" {
inline = [
"sudo apt-get -y update",
"sudo apt-get -y install nginx",
"sudo service nginx start"
]
}
# Day 1 through Day N configurations - tool like Chef, Ansible, Docker, etc
provider "chef" {
server_url = "https://api.chef.io/organization/example"
run_list = [ "recipe[example]" ]
}
IaC Makes Infrastructure More Reliable
- IaC makes changes idempotent, consistent, repeatable, and predictable.
- Without IaC, (우윀…🤮)
- scaling up infrastructure to meet increased demand may require an operator to remotely connect to each machine and then manually provision and configure many servers by executing a series of commands/scripts.
- They might open multiple sessions and move between screens, which often results in skipped steps or slight variations between how work is completed, necessitating rollbacks.
- Perhaps a command was run incorrectly on one instance and reverted before being re-run correctly.
- These process inconsistencies can result in slight differences between servers that compound over time and could impact their performance, usability, or security.
- If a large team is applying changes, the risks increase because individuals don’t always follow the same instructions identically.
- With IaC,
- we can test the code and review the results before the code is applied to our target environments.
- Should a result not align to our expectations, we iterate on the code until the results pass our tests and align to our expectations.
- Following this pattern allows for the outcome to be predicted before the code is applied to a production environment.
- Once ready for use, we can then apply that code via automation, at scale, ensuring consistency and repeatability in how it is applied.
- Since code is checked into version control systems such as GitHub, GitLab, BitBucket, etc., it is possible to review how the infrastructure evolves over time.
- The idempotent characteristic provided by IaC tools ensures that, even if the same code is applied multiple times, the result remains the same.
IaC Makes Infrastructure More Manageable
- Leveraging HashiCorp Terraform IaC provides benefits that enable mutation, when necessary, via code.
- During execution,
- Terraform will examine the state of the currently running infrastructure, determine what differences exist between the current state and the revised desired state, and indicate the necessary changes that must be applied.
- When approved to proceed, only the necessary changes will be applied, leaving existing, valid infrastructure untouched.
IaC Makes Sense
- Successfully managing the lifecycle of infrastructure is hard, and the impact of poor management decisions can be significant, ranging from financial and reputational losses to even loss of life when considering government and military dependencies on infrastructure.
- Adopting the use of an IaC tool such as HashiCorp Terraform, in conjunction with related and established tools, processes, and workflows, is a necessary step in mitigating these risks.
Describe advantages of IaC patterns:
What is infrastructure as code and why is it important?
Learn why "infrastructure as code" is the answer to managing large-scale, distributed systems, cloud-native applications, and service-based architectures.
www.hashicorp.com
- Learn why "infrastructure as code" is the answer to managing large-scale, distributed systems, cloud-native applications, and service-based architectures.
- Infrastructure as code is a mainstream pattern for managing infrastructure with configuration files rather than through a graphical user interface or through manual command line script sequences.
- It allows you to build, change, and manage your infrastructure in a safe, consistent, trackable, and repeatable way by defining resource configurations that you can version (in a version control system like GitHub), reuse, and share.
Understand the purpose of Terraform (vs other IaC)
Explain multi-cloud and provider-agnositc benefits:
https://developer.hashicorp.com/terraform/intro/use-cases#multi-cloud-deployment
Use Cases | Terraform | HashiCorp Developer
Learn how Terraform enables multi-cloud deployments, application management, policy compliance, and self-service infrastructure.
developer.hashicorp.com
- Provisioning infrastructure across multiple clouds increases fault-tolerance, allowing for more graceful recovery from cloud provider outages.
- However, multi-cloud deployments add complexity because each provider has its own interfaces, tools, and workflows.
- Terraform lets you use the same workflow to manage multiple providers and handle cross-cloud dependencies.
- This simplifies management and orchestration for large-scale, multi-cloud infrastructures.
https://developer.hashicorp.com/terraform/tutorials/networking/multicloud-kubernetes
Deploy federated multi-cloud Kubernetes clusters | Terraform | HashiCorp Developer
Use Terraform to provision Kubernetes clusters in the Azure and AWS clouds, deploy Consul Helm charts enabling Consul federation, and deploy an example application on both clusters.
developer.hashicorp.com

- k8s clusters in both AWS and Azure environments
- Consul federation → mesh gateways across the two clusters using the helm porvider
Application Infrastructure Deployment, Scaling, and Monitoring Tools
- You can use Terraform to efficiently deploy, release, scale, and monitor infrastructure for multi-tier applications.
- N-tier application architecture lets you scale application components independently and provides a separation of concerns.
- An application could consist of a pool of web servers that use a database tier, with additional tiers for API servers, caching servers, and routing meshes.
- Terraform allows you to manage the resources in each tier together, and automatically handles dependencies between tiers.
- For example, Terraform will deploy a database tier before provisioning the web servers that depend on it.
https://developer.hashicorp.com/terraform/tutorials/applications/datadog-provider
Automate monitoring with the Terraform Datadog provider | Terraform | HashiCorp Developer
Create metrics and endpoint monitors for a pre-configured Kubernetes cluster with the Helm and Datadog Terraform providers.
developer.hashicorp.com
https://developer.hashicorp.com/terraform/tutorials/aws/blue-green-canary-tests-deployments
Use Application Load Balancers for blue-green and canary deployments | Terraform | HashiCorp Developer
Configure AWS application load balancers to release an application in a rolling upgrade with near-zero downtime. Incrementally promote a new canary application version to production by building a feature toggle with Terraform.
developer.hashicorp.com
Self-Service Clusters
- At a large organization, your centralized operations team may get many repetitive infrastructure requests.
- You can use Terraform to build a "self-serve" infrastructure model that lets product teams manage their own infrastructure independently.
- You can create and use Terraform modules that codify the standards for deploying and managing services in your organization, allowing teams to efficiently deploy services in compliance with your organization’s practices.
- HCP Terraform can also integrate with ticketing systems like ServiceNow to automatically generate new infrastructure requests.
https://developer.hashicorp.com/terraform/tutorials/modules/module-use
Use registry modules in configuration | Terraform | HashiCorp Developer
Use modules from the public Terraform Registry to define an Amazon VPC containing two EC2 instances. Select module and root input and output variables, install the modules, and apply the configuration.
developer.hashicorp.com
https://developer.hashicorp.com/terraform/tutorials/modules/module-create
Build and use a local module | Terraform | HashiCorp Developer
Write a local module to create an Amazon S3 bucket hosting a static website. Create a module directory, write the module configuration, variables, and outputs, and call the module from a root configuration.
developer.hashicorp.com
- Build and use a local module
Setup Instructions - ServiceNow Service Catalog Integration - HCP Terraform | Terraform | HashiCorp Developer
ServiceNow integration enables your users to order Terraform-built infrastructure from ServiceNow.
developer.hashicorp.com
Policy Compliance and Management
- Terraform can help you enforce policies on the types of resources teams can provision and use.
- Ticket-based review processes are a bottleneck that can slow down development.
- Instead, you can use Sentinel, a policy-as-code framework, to automatically enforce compliance and governance policies before Terraform makes infrastructure changes.
- Sentinel policies are available in Terraform Enterprise and HCP Terraform.

https://developer.hashicorp.com/terraform/tutorials/cloud-get-started/cost-estimation
Control costs with policies | Terraform | HashiCorp Developer
Write a soft-mandatory Sentinel policy against example infrastructure to limit its cost to less than one hundred dollars a month.
developer.hashicorp.com
https://developer.hashicorp.com/terraform/tutorials/cloud-get-started/cost-estimation
Control costs with policies | Terraform | HashiCorp Developer
Write a soft-mandatory Sentinel policy against example infrastructure to limit its cost to less than one hundred dollars a month.
developer.hashicorp.com
https://developer.hashicorp.com/terraform/cloud-docs/policy-enforcement
Policy Enforcement - HCP Terraform | Terraform | HashiCorp Developer
Policies are rules that HCP Terraform enforces on Terraform runs. Use Sentinel and OPA to validate plans before Terraform provisions infrastructure.
developer.hashicorp.com
Software Defined Networking
- Terraform can interact with Software Defined Networks (SDNs) to automatically configure the network according to the needs of the applications running in it.
- This lets you move from a ticket-based workflow to an automated one, reducing deployment times.
https://developer.hashicorp.com/consul/tutorials/network-automation/consul-terraform-sync
Automate your network configuration with Consul-Terraform-Sync | Consul | HashiCorp Developer
Automate updates to firewall rules in network infrastructure with Consul-Terraform-Sync.
developer.hashicorp.com
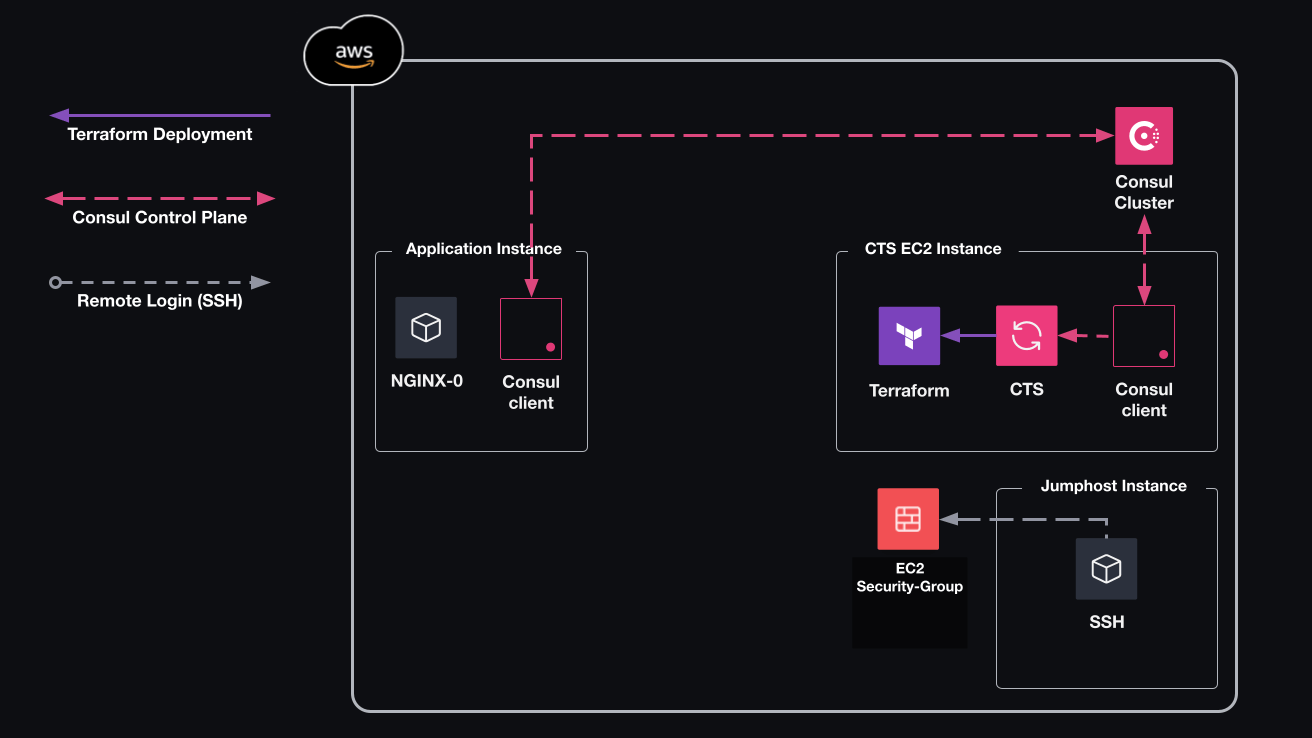
https://developer.hashicorp.com/consul/docs/nia/network-drivers
Network Drivers | Consul | HashiCorp Developer
Consul-Terraform-Sync Network Drivers with Terraform and HCP Terraform
developer.hashicorp.com
- Consul-Terraform-Sync (CTS) uses network drivers to execute and update network infrastructure.
- Drivers transform Consul service-level information into downstream changes by processing and abstracting API and resource details tied to specific network infrastructure.
Kubernetes
- Kubernetes is an open-source workload scheduler for containerized applications.
- Terraform lets you both deploy a Kubernetes cluster and manage its resources (e.g., pods, deployments, services, etc.).
https://github.com/hashicorp/terraform-k8s
GitHub - hashicorp/terraform-k8s: Terraform Cloud Operator for Kubernetes
Terraform Cloud Operator for Kubernetes. Contribute to hashicorp/terraform-k8s development by creating an account on GitHub.
github.com
- k8s operator for terraform
https://developer.hashicorp.com/terraform/tutorials/kubernetes/kubernetes-provider
Manage Kubernetes resources via Terraform | Terraform | HashiCorp Developer
Schedule a NGINX instance and expose it using the Terraform Kubernetes Provider. Configure the provider to access the cluster manually or based on kubectl context. Schedule and scale a deployment, and schedule a service.
developer.hashicorp.com
https://developer.hashicorp.com/terraform/tutorials/kubernetes/kubernetes-operator
Deploy infrastructure with the Terraform Cloud Kubernetes Operator v1 | Terraform | HashiCorp Developer
Use the Terraform Cloud Operator for Kubernetes to manage the lifecycle of cloud and on-prem infrastructure through a single Kubernetes custom resource. Provision an AWS SQS message queue as a prerequisite for an application on Kubernetes.
developer.hashicorp.com

- You can create application-related infrastructure from a Kubernetes cluster by adding the Operator to your Kubernetes namespace.
- The Operator uses a Kubernetes Custom Resource Definition (CRD) to manage HCP Terraform workspaces.
- These workspaces execute an HCP Terraform run to provision Terraform modules.
- By using HCP Terraform, the Operator leverages its proper state handling and locking, sequential execution of runs, and established patterns for injecting secrets and provisioning resources.
Parallel Environments
- You may have staging or QA environments that you use to test new applications before releasing them in production.
- As the production environment grows larger and more complex, it can be increasingly difficult to maintain an up-to-date environment for each stage of the development process.
- Terraform lets you rapidly spin up and decommission infrastructure for development, test, QA, and production.
- Using Terraform to create disposable environments as needed is more cost-efficient than maintaining each one indefinitely.
Software Demos
- You can use Terraform to create, provision, and bootstrap a demo on various cloud providers.
- This lets end users easily try the software on their own infrastructure and even enables them to adjust parameters like cluster size to more rigorously test tools at any scale.
Explain the benefits of state:
https://developer.hashicorp.com/terraform/language/v1.1.x/state/purpose
State | Terraform | HashiCorp Developer
Terraform must store state about your managed infrastructure and configuration. This state is used by Terraform to map real world resources to your configuration, keep track of metadata, and to improve performance for large infrastructures.
developer.hashicorp.com
Understand Terraform basics
Install and version Terraform providers:
https://developer.hashicorp.com/terraform/language/v1.1.x/providers/configuration
Provider Configuration - Configuration Language | Terraform | HashiCorp Developer
Learn how to set up providers, including how to use the alias meta-argument to specify multiple configurations for a single provider.
developer.hashicorp.com
https://developer.hashicorp.com/terraform/language/settings#specifying-provider-requirements
Terraform Settings - Configuration Language | Terraform | HashiCorp Developer
The terraform block allows you to configure Terraform behavior, including the Terraform version, backend, integration with HCP Terraform, and required providers.
developer.hashicorp.com
https://developer.hashicorp.com/terraform/language/files/dependency-lock
Dependency Lock File (.terraform.lock.hcl) - Configuration Language | Terraform | HashiCorp Developer
Terraform uses the dependency lock file .teraform.lock.hcl to track and select provider versions. Learn about dependency installation and lock file changes.
developer.hashicorp.com
Write Terraform configuration using multiple providers:
https://developer.hashicorp.com/terraform/language/providers/configuration
Provider Configuration - Configuration Language | Terraform | HashiCorp Developer
Learn how to set up providers, including how to use the alias meta-argument to specify multiple configurations for a single provider.
developer.hashicorp.com
Describe how Terraform finds and fetches providers:
https://developer.hashicorp.com/terraform/language/v1.1.x/providers/configuration
Provider Configuration - Configuration Language | Terraform | HashiCorp Developer
Learn how to set up providers, including how to use the alias meta-argument to specify multiple configurations for a single provider.
developer.hashicorp.com
참고사항:
Providers - Configuration Language | Terraform | HashiCorp Developer
An overview of how to install and use providers, Terraform plugins that interact with services, cloud providers, and other APIs.
developer.hashicorp.com
https://registry.terraform.io/browse/modules
Terraform Registry
registry.terraform.io
Input Variables - Configuration Language | Terraform | HashiCorp Developer
Input variables allow you to customize modules without altering their source code. Learn how to declare, define, and reference variables in configurations.
developer.hashicorp.com
Deploy federated multi-cloud Kubernetes clusters | Terraform | HashiCorp Developer
Use Terraform to provision Kubernetes clusters in the Azure and AWS clouds, deploy Consul Helm charts enabling Consul federation, and deploy an example application on both clusters.
developer.hashicorp.com
https://developer.hashicorp.com/tutorials
Tutorials | HashiCorp Developer
Start learning with step-by-step, hands-on, command-line tutorials, videos, and hosted terminal sessions. Actionable examples help you learn to provision, secure, connect, or run any application on any infrastructure.
developer.hashicorp.com
Terraform Associate 자격증을 준비하는 분들에게 도움이 되셨으면 좋을 것 같습니다!
긴 글 읽어주셔서 감사합니다 🤗
행복한 연휴 마무리 하시고 5월도 화이팅 하시와요!!!
'Terraform > Terraform Associate Study' 카테고리의 다른 글
| Terraform Associate Study - 20240512 - 3주차 (0) | 2024.05.19 |
|---|---|
| Terraform Associate Study - 20240428 - 1주차 (0) | 2024.05.05 |
| Terraform Associate Study - 20240421 - OT (0) | 2024.05.01 |
